According to recent statistics, 60% of small to medium enterprises experience data breaches a year. It is a sad reality that cyberattacks are kept on increasing and have become one of the most pressing problems facing small and medium-sized businesses (SMBs) today.
However, many companies don’t know how to protect themselves. All companies need to understand hackers' risk to their systems and data. There is no way to guarantee 100% security, but there are several measures you can take to limit your chances of becoming an attack target. This guide will cover many important aspects to help you understand and protect your small to medium business from hacking and cyberattacks.

Cyber Attacks on Businesses
Cybersecurity experts have warned about the threat of a so-called “cyber 9/11,” but many business leaders still aren’t taking it seriously. That’s a mistake because hackers and other cybercriminals are constantly targeting businesses. And one way they do that is by attacking the computers of people who work in the businesses.
To help you understand the threat to your company, let’s look at the most common cyber attacks at work. The most common type of attack on a company’s computer system is a “workplace hack.” These are generally done by someone with unauthorized access to the network — whether a hacker or an employee who accidentally gets into the system. Sometimes, an attacker will use a vulnerability in a piece of software.
When an attacker gains access to multiple accounts, they can change passwords and other security settings to control the system for a long time. Once an attacker has access to a system, they may install malware or spyware to steal data or use the system for more malicious purposes. This could include installing ransomware or other types of malware that encrypt your files or using the network to transmit spam messages to people who have downloaded viruses.
Hackers may also attempt to gain access to sensitive files that can be used to steal data or perform other types of attacks. Vulnerabilities in a company’s products are also possible. Against all these odds, cybersecurity is in need of an hour.
Cybersecurity Matters

Cybersecurity is a broad term, and the definition of cybersecurity is changing every day. It’s essential to understand the meaning behind “cybersecurity” so you know what you need to protect yourself from. The most basic definition of cybersecurity is using technologies and practices to protect against cyber attacks. This includes protecting against internal attacks within your business and external attacks from outside sources.
The number of cybersecurity incidents reported by U.S. businesses continues to rise and is expected to reach $6 trillion in 2018. Businesses must understand how to defend their networks against cyberattacks and maintain their data security. Cybersecurity is an important issue for businesses because they want to keep confidential customer information private, but they also want to ensure the integrity of sensitive business systems.
Cybersecurity protects information systems (including people) from malicious actions by individuals and groups, such as computer hacking, spamming, and phishing.
According to a recent survey of global business executives, the number one security threat businesses face is cyberattacks.
Opportunities for Cyber Criminals
Lack of expertise
The lack of experts in cyber security is one of the biggest problems that make it difficult for many organizations to prevent cyberattacks. Most companies and governments cannot hire the right people, and the ones they do hire are either too expensive or have insufficient skills to perform their jobs.
Cybercriminals know this, so they are more motivated to launch attacks, which can be costly to businesses and government organizations. But even if you have a team of cybersecurity experts in place, you may still be at risk. Cybercriminals have become smarter, using more sophisticated tools to steal data and information.
You need to be aware of these tools to defend your company and protect yourself. The best way to protect yourself from cyberattacks is to develop a comprehensive strategy for cyber defense. You need to create a plan for security that includes both technical and non-technical aspects.
Lack of data management
In today’s world, data is a significant asset for any business. If you lose it, you can’t get it back. It is important to ensure that your company’s data is secured. With the proper data management, you can protect your company’s data and ensure that your business is not affected by data leaks.
Your company’s data must be adequately secured. If you don’t do this, you may face many problems. For example, your company’s data may be leaked to hackers and used in other malicious activities. You may also lose customers as they may find your data insecure.
The report of the Ponemon Institute mentioned that the average cost of a data breach is $3.86 million, and this figure will rise as the year progresses.
This is due to the increasing use of mobile devices and the growing number of organizations that store sensitive information online. This increase in cybercrime has led to the rise of a new breed of cybercriminals: the “botnet” or zombie network of computers used for cyber attacks. A botnet can steal your easily, putting you in a vulnerable crisis situation.

Usage of Cloud-Based Technologies
Many businesses are now using cloud-based applications to improve efficiency and reduce costs. However, there is a risk that your data is stored outside your control. A recent study by Cisco revealed that many small businesses have no security policies for cloud-based services.
Cybercriminals take advantage of the lack of security on cloud-based applications. If you use cloud-based applications, you need to ensure that your data is protected. If you use cloud-based applications, you should make sure you’re always using the latest version.
The latest version will have been updated to address any known vulnerabilities. Make sure you check if there have been any updates to your version and install them as soon as possible.
Aftermaths of Cyber Attacks
Monetary loss
Companies are increasingly being hit by cyberattacks that can compromise their most valuable assets, including customer information and trade secrets. They're also suffering financially from cyber attacks that disrupt their operations. And they're paying for cyber insurance to protect against these losses.
As per National Cyber Security Alliance, more than 50 percent of small businesses have experienced a data breach; nearly half of them were seriously affected, with at least one business closing or laying off staff.
Damage of Reputation
Any system breach can cause significant harm to a company’s public image. The hackers send a confidential email to your client base, letting them know that their private data was stolen. Their personal financial and identifying information has been taken from your website.
As a result, the reputation of the company is damaged. This is the same for your clients. When your clients find out about this breach, they’ll most likely think that you were negligent in protecting their private information.
If your business depends on customer trust and confidence, you must keep your clients informed of any data breaches. When you discover a data breach, you’ll need to determine whether or not your customers have been affected.
If your business is involved in a data breach, you may want to notify your customers via email and social media posts. You should also contact the relevant authorities to alert them of the violation. In some cases, this may mean getting law enforcement or even your state’s attorney general.
Decreasing Productivity
Cyber breaches highly affect the productivity of a company. Whether some businesses may be able to survive a brief downtime, others will have no choice but to shut down if their operations are disrupted for more than a few hours.
As soon as you start to accept interruptions as part of your job, your work will be severely impacted, productivity will drop significantly, and your employees will be less effective. The time required to complete the project will harm productivity and momentum, so you'll need to speed up your schedule and take action as soon as possible.
sensitive data Exposure

These sensitive data include the financial details of employees and the company. In several ways, a hacker can hack into your company’s system and steal your company’s data.
Hackers are always looking for new ways to get in and access sensitive data. So you must protect your website and make sure that your company’s data is not compromised.
- A hacker can hack data by SQL Injection. This is a web application vulnerability. A hacker can access your data by changing the data entry fields to SQL commands. The hacker will enter a special code or URL into the field to send the SQL command to the database.
- XSS Attack Hackers can access sensitive information such as usernames, passwords and other personal data. They change the website's source code to display its malicious message. These messages are usually targeted at the users who are logged into the website.
- Social Engineering Hackers trick you into sharing sensitive information with them. The hacker may send a fake email that looks like it was from your company’s email service provider. When the recipient clicks on the link, the hacker will be able to access the user’s sensitive data.
- Phishing Hackers steal information by impersonating a trusted organization. A hacker sends an email that looks similar to an official email sent by your company. It contains a link to a website where they can enter the data. The email may look like it came from the IT department or an HR department and may contain a link to an employee portal or a payment portal.The hacker may also pretend to be an employee and ask the user to log in to a particular website. Once the user enters their credentials, the hacker will access the user’s information.
Cyberthreats to Small and Medium Businesses
Malware Attack
Malware includes any software that performs unwanted or malicious activities on a computer. Malware attacks on small and medium businesses (SMBs) continue rising, and these organizations are trying hard to protect themselves against such attacks.
A recent survey found that more than two-thirds of SMBs have been hit by malware, and one in five have experienced a data breach.
There are several different reasons why Cybercriminals target sMBs.
These attacks often succeed because of poor network defenses and the lack of a secure email policy. While it’s easy to blame hackers for these breaches, other potential causes are.
According to a report by McAfee, SMBs are often targeted because they are easier to penetrate. This is due to their smaller size, weaker security posture, and limited resources.
In addition, many SMBs rely on third-party suppliers or contractors, which can expose them to additional risk. SMBs need to take immediate action to protect themselves from cybercrime.
Types of malware attacks
Malware comes in all shapes and sizes. It can be a simple piece of executable code (software) that you download or a virus, worm, Trojan horse, or malware. It can even be something like spyware, which is software that gathers information about you.
There are many types of malware, and each type is usually associated with a particular purpose. The most common types of malware are
- Viruses
- Worms
- Trojans
- Spyware
- Adware
- Rootkits

How Malware Infect
Let's take a quick look at how malware gets into your computer. Malware is usually spread via email attachments or over the Internet. However, there are other ways to get it into your system.
It can also be brought to your computer by visiting infected websites or installing software contaminated with malware. For example, if you download a file off the Web and save it to your computer, you're opening yourself up to infection.
Phishing Attacks
The cyber security needs of small and large companies are almost the same. Small organizations are also at a higher risk of becoming victims of cybercrime because they may not have the resources to fight back.
Phishing attacks are so common that they’ve become a part of our everyday lives. We use our smartphones for everything, including banking, shopping, and even paying bills. Phishing attacks are becoming increasingly sophisticated. This means that you need to be vigilant and stay updated on the latest ways to protect yourself from them.
If you do not take the necessary steps, your business is against such attacks; they could cost you more than money. If your business relies on online transactions or any other type of electronic communication, you need to be aware of this kind of attack.
Phishing Email
A phishing email attempts to trick the recipient into giving up their username or password in exchange for something else. For example, a company might send out an email saying it has detected a problem with payment and asks for a username and password.
When users click on the links in these emails, they can be infected with malware or tricked into providing sensitive information such as login credentials. There are many ways to deliver these messages. People can send them through a website, instant messaging, email, or even phone calls.
Phishing scams can be highly effective because they rely on people’s natural desire to help others. If they’re perfect, phishing emails can appear almost identical to real emails, even using the same language and formatting. But while they may look similar, the contents are entirely different.
Phishing emails usually ask for information you wouldn’t normally need to provide, such as your username and password. The main objective of a phishing attack is to steal personal information from your customers and employees.
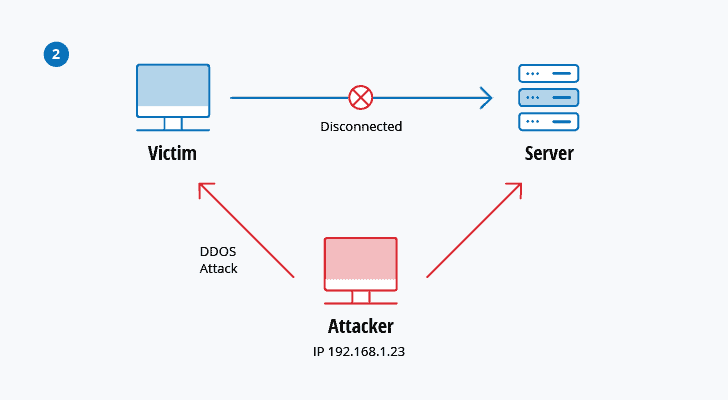
Distributed Denial of Service (DDoS)
A DoS (denial-of-service) attack occurs when someone attacks your computer or network and disrupts services. Attackers use multiple computers to send the traffic or data.
The user often won’t realize that their computer is being used in a distributed denial-of-service attack (DDoS). These attacks primarily target large companies, sometimes as protests against governments or individuals.
Inexpert Human Resource
While not all cyber-vulnerabilities are caused by social engineering, human behavior is also the most significant cybersecurity factor.
The 2019 Verizon DBIR states that end-user error is the number one threat to businesses’ security.
Poor password practices and clicking on malicious links are just a couple of the behavioral vulnerabilities end users fall victim to regularly. Businesses are vulnerable to social engineering attacks, and end-users need to be educated and trained to protect their sensitive information.
Phishing is the initial point of attack for many organizations, and they often use this approach because it is a low-cost and risky strategy.
Video-teleconferencing threats
During the current COVID-19 pandemic, teleconferencing has forced many companies and individuals to use video-teleconferencing as a primary communication tool. Historically, small businesses have relied on these tools to support virtual offices and remote employees.
While large numbers of people are turning to video-teleconferencing (VTC) platforms to stay connected, reports of VTC hijacking (also called “Zoom-bombing”) are emerging worldwide.
Several reports have shown that conferences have been disrupted by pornography and hate language. It would be advisable to ask those in charge to take the necessary steps.
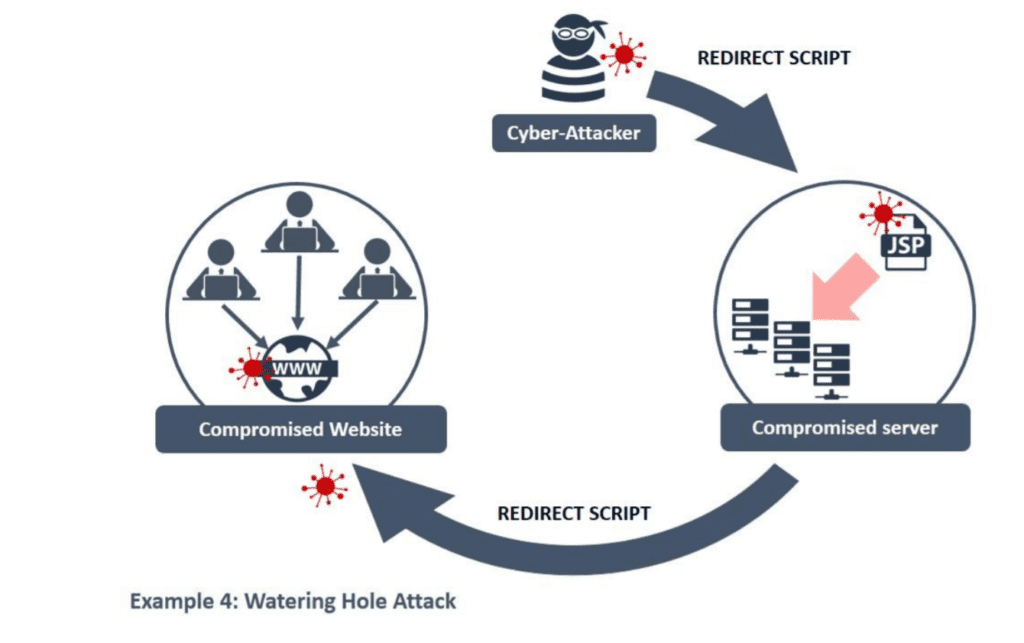
Watering Hole Attack
The goal here is to deliver malware to affect the victims who are more likely to want to buy from your site. If you think about it, watering hole attacks happen when an attacker targets websites frequently used by group members.
They can infect websites with malware as a trap. Eventually, one of the group members will become infected, and from there, they'll gain access to the entire network. Several people who had visited the infected website were exposed, so this kind of attack is tough to trace.
Brute Force Attack
It's a password attack. A password is a form of protection used to ensure that only authorized individuals access an account or resource. Brute force is when you just try every combination until you find the right one.
This password-cracking algorithm is not human, and it can take months or even years to crack a single password. So, it's essential to create strong passwords, including upper and lower-case letters, numbers, and symbols, and change them regularly.
You need Overall Protection: Ways to remove vulnerabilities
Perform security risk Analysis
A cyber information security risk assists in evaluating the information and drives you need to protect your business's sensitive data.
It determines where to allocate the appropriate resources; identify the steps you need to take to mitigate risks, and understand the most appropriate level of technology required for your business.
It also locates what is your business's most important data assets in terms of customer information and what significant impacts will a data breach have on your business?
Conduct A Vulnerability Scan
An effective vulnerability scan will help to reveal potential security vulnerabilities in your system. You can do it yourself with a low-cost consumer-level scanner or an IT expert to use a more sophisticated enterprise-level product.
Equally important, you should know what to look for in a vulnerability scan. How does a vulnerability scan work?
A vulnerability scan works by probing your system to see if it can identify potential vulnerabilities. A vulnerability scan can identify several different types of vulnerabilities, including:
- Web server vulnerabilities
- Application server vulnerabilities
- File server vulnerabilities
- Network device vulnerabilities
- Directory traversal vulnerabilities
- Buffer overflow vulnerabilities
- File inclusion vulnerabilities
- Web server vulnerabilities
A quick scan of your computer systems should uncover the following:
- What methods are running?
- Are there known vulnerabilities in those systems?
- Are there unknown vulnerabilities in those systems?
- What ports are open?
- What are services running?
- What protocols are running?
- Are there any hidden processes?
- What is the level of trust in the systems?
A scan can also help you identify possible security breaches in your systems. For example, if your organization has a web server, it might be wise to run a scan to ensure that no known vulnerabilities are present.

Implement Security Controls
Once you have completed risk analysis, now is the time to implement risk controls. You need to take specific measures to control or mitigate cyber attacks.
Enable Business Grade Firewalls
The firewall performs functionalities for detecting and preventing intrusions. The best security tools include anti-malware, anti-virus, and other constantly updated services to guard against newly discovered threats.
Why is a next-generation firewall important? As businesses increasingly adopt cloud computing, they need to protect their data in the cloud and on the mobile devices used by employees. This means that security needs to extend beyond traditional network boundaries, such as the perimeter.
As more applications move to the cloud, it becomes harder for organizations to protect their networks. A next-generation firewall provides a complete solution to this challenge. The firewall can monitor all traffic in and out of an organization’s network, regardless of its location.
Back-Up Work Data
Surprisingly, most people don’t back up their data. If you are also among those, you are making a big mistake. Be sure you have a plan for what to do if you lose your data. This can be a major hassle, so it’s essential to have a backup plan.
How do you back up? You should have an offsite server or cloud service in place to make sure you can quickly and easily restore a backup from a safe location, like an offsite server or even a cloud service for backup.
Use Complex passwords
Use complex and lengthy passwords to protect your business from cyber threats. Password management is a critical task for every business. A good password manager will help you protect your business from cyber threats.
If your business uses a simple password, it’s easy for cyber attackers to access your business. This can be very dangerous for your business. So, you should make sure that you have a complex password.
A complex password is a password of numbers, letters, symbols and special characters. It’s a solid password. A complex password is an excellent way to protect your business from cyber threats.
Password should contain at least one of the following:
- Number (e.g., 12345678)
- Letter (e.g., qwerty)
- Symbol (e.g.!@#$%^&*())
- Dictation (e.g., “I love dogs” or “I love my children”)
- Character (e.g. (, ), {, }, |, \, etc.)
- Punctuation (e.g.., :,?,!,?, :, -, /, &, ;, “)
- Hexadecimal (e.g. F0-F9)
- Random (e.g. “YOGI”, “aYB” or “GAMBA”)
Formulate Mobile device management policy

Whether you’re giving your employees cell phones to use for work or have a Bring Your Device (BYOD) policy, employees are likely using mobile devices to access company information (like email and sensitive line-of-business applications).
You need a mobile device policy to protect your business from employee data loss. You should also provide training to your employees to avoid using their devices to download or access information without your consent.
Setting policies at the device level is a must. Requirements like setting a passcode and encrypting passwords will keep things secure.
Use Multi-factor authentication
Formerly known as Two-factor authentication, Multi-factor authentication (MFA) is a technology that adds an extra layer of security to your website by requiring a user to supply both a username and a password and then the second piece of information such as a one-time password (OTP), token or mobile number.
Use Multi-factor authentication to protect your critical data against malicious software and cyber attacks.
Imagine a malicious user trying to access your website using a stolen username and password combination. Without MFA, they would be able to log in and start posting comments or viewing sensitive information.
As a small business, you can protect yourself by adding MFA to your website and using a free service such as Google Authenticator to generate OTPs for your users.
Multi-factor authentication is the most common way to protect your business. It's free, easy to use and can be integrated into your website. However, you can also use MFA with other technologies such as SMS, email, phone calls, etc.
Control Removable Storage
Media card readers and USB flash drives are often the easiest to insert malware into a computer system. You need to get your office computers under control, and you need to do it right away. Do not let employees put information on removable like USB flash drives and memory cards.
You need to do a thorough review of the devices used in your office. There are many ways that malware can be inserted into a computer system. One of the easiest ways is to use an unsecured or unprotected device to insert the malware. Use malware protection for all your devices to keep them secured.

Review Network Architecture
As we all know, many different cyberattacks are going on every day. It is tough to get away from such attacks. We should have an exemplary architecture for our business network to protect it from attackers.
- Update Software: You should also update all the software on your PC to the latest version. This will ensure that your system is protected from any threats and vulnerabilities.
- Change Your Passwords: Change all your passwords on your PC and online accounts so that no one else can access them. Make sure that you change your passwords frequently, as this is the best way to protect your data.
- Clean Up Files and Folders: Delete unnecessary files and folders on your PC.
- Remove Malware: If you are infected with a virus, it will be hard to remove it manually. If you are not an expert in computer technology, we can recommend you use a professional anti-malware program to clean up your computer system.
Use Virtual Private Network
Previously, a VPN is used for securing the data and information in a local network. However, today, a VPN is used to secure the data and information on the internet. The most important benefits of a VPN are:
- Protection against all types of cyberattacks: A VPN is a tool to protect against cyberattacks, such as hacking, spyware, and viruses.
- Security: A VPN provides you with security that is not available on the internet. This is because it hides your IP address and provides you with a new IP address.
- Remote Access: A VPN can also access your home or office from anywhere.
- Secure Email: A VPN can also secure your email by encrypting the data.
- Unlimited Data: A VPN can be used to transfer data from one computer to another without worrying about the size of the data.
VPNs are often confused with proxies, but the two are pretty different. Proxies are usually used to access blocked websites, while VPNs are typically used to access the internet.
VPNs are also more secure than proxies. Proxies are only encrypted if you connect to them over an encrypted connection (usually HTTPS), whereas VPNs are typically encrypted. Proxies also are easily detected, whereas VPNs are harder to see.
Some recommended VPNs are ExprssVPN, NordVPN, Surfshark VPN and CyberGhost VPN.
One of them is ExpressVPN.
ExpressVPN is an excellent choice for anyone looking to unblock websites or countries, access geo-blocked content, or browse the internet anonymously. We highly recommend this VPN for anyone looking for a secure, reliable VPN service.
You can read our full review of ExpressVPN here. ExpressVPN is a popular VPN provider that offers many high-quality VPN servers in over 100 different countries. It also has an excellent customer support team who are always ready to help and guide you through any issues you may have.
ExpressVPN was founded in 2006 by Alan Mamo, a software engineer with a passion for security and privacy. ExpressVPN offers a range of products, including a free VPN service and premium VPN services that come with various monthly and yearly plans.
All of the VPN services provided by ExpressVPN come with the highest level of encryption and security, with advanced protocols and features to ensure the safety and security of your data.
Prevent Against Ransomware
If you are reading this, you’ve been affected by a ransomware attack. It has probably affected your work or personal life. It could have affected your bank account. It is essential to understand that there is no going back once the ransomware has infected your computer.
Once the encryption process is complete, you’re left with a locked-down machine that won’t boot unless you pay the ransom. But don’t panic!
- Use anti-virus software, and update it regularly.
- Back up your data regularly, and don't forget to do it when traveling.
- Set a strong password.
- Don't click on links or open attachments you aren't expecting.
- Don't log into accounts you aren't sure you own.
- Don't use unsecured public Wi-Fi networks, and if you do, use a strong password.
- You can use the built-in Windows tools to remove it, like Antivirus Software. Many anti-virus programs have built-in utilities that can help you remove malware. This is usually done in a separate utility called the “Anti-Malware” utility. For example, Microsoft Security Essentials includes an Anti-malware tool. It's located under the “Tools” menu.
- You should also remove any other programs installed with the infected software. This may include programs bundled with the malware and any other programs you downloaded.
Implement employee monitoring
Train your employees
A good first line of defense against cybersecurity attacks is to train employees to spot the signs of an attack and take immediate steps to prevent it. If you don’t train your staff to recognize and respond to cyberattacks, they can cause damage before you even realize something is wrong.
Compared to other IT issues, such as a failed server, employees are often less likely to know how to respond to an attack. To ensure that your employees know how to identify and respond to a cyberattack, you need to educate them about the risks and recognize the symptoms of an attack.
This means getting them familiar with the risks and making sure they understand what to do in the event of an attack. You should also educate them about the available tools to detect and respond to attacks. They can respond to an attack before it escalates by providing them with the right tools.
The next step is to train them to respond to an attack. Teach them to take the following steps:
- Identify the threat. Employees need to know what an attack looks like to identify and respond to it.
- Respond to the threat. Employees need to know what to do when they detect an attack.
- You can train your employees by providing them with the right tools and resources. The following tools can help them respond to an attack.
Remove Employee Weaknesses
Help your employees do their jobs effectively and securely. They need access to reliable email and storage. Whether their job requires them to send confidential information or if their company is part of the federal government, people who work in this field will need encrypted email.
You also need to have a clearly outlined policy on how to handle your company data. Policies should describe how employees can access company data and how they should interact with it. Guidelines should be clear and concise and must be followed strictly. It’s essential that they are enforced effectively as well. You can even execute a security policy and have it turn on automatically. If you're an Office 365 user, you can implement data loss prevention policies in Outlook and other apps.
This tool ensures that the customer’s personal information, like their name, email address, and credit card number, will remain private and only be used inside the organization.
Hire the best resource
Employees are the main thing that determines whether or not you will be a success or failure. It takes more than just the right product and pricing to have an effective online store. You need the right team to achieve the best results.
. Create a Cybersecurity Policy-In most cases, you don’t need to hire a full-time cybersecurity specialist. Instead, you need to identify an individual or a team that can perform the following functions:
- Identify potential threats to the organization
- Determine the impact of the threats
- Define the response to each threat
- Develop a mitigation plan; Maintain a system for monitoring and reporting
- Ensure compliance with any regulations and standards
- Provide a framework for evaluating cybersecurity solutions.
With the training of employees, dedicated a portion or department of IT to look for cyber risks and ways to counter them.
Conclusion
As you build your business, you need to start thinking about cybersecurity like you think about sales, email, customer service, or anything else you do to reach your customers.
Make it a priority and focus your efforts accordingly. It’s a numbers game, and your biggest number will be your bottom line. If you spend money on cyber hygiene, you will make more money from your business.
While cybersecurity is a complex subject, it doesn’t have to be overwhelming. The first step is to identify your security needs. Think about the areas of your business where you need the most protection—it could be a web server, a database server, or your mobile device.
Then, ask yourself questions like: Who has access to this data? What’s the sensitivity of this data? What are you using this data for? What are the consequences of an intrusion into your system? These questions will help you prioritize your needs.
Read the rest of this guide to learn about the basics of cybersecurity. To retain the overall security of your small and medium businesses, read any of our recommended VPNs.